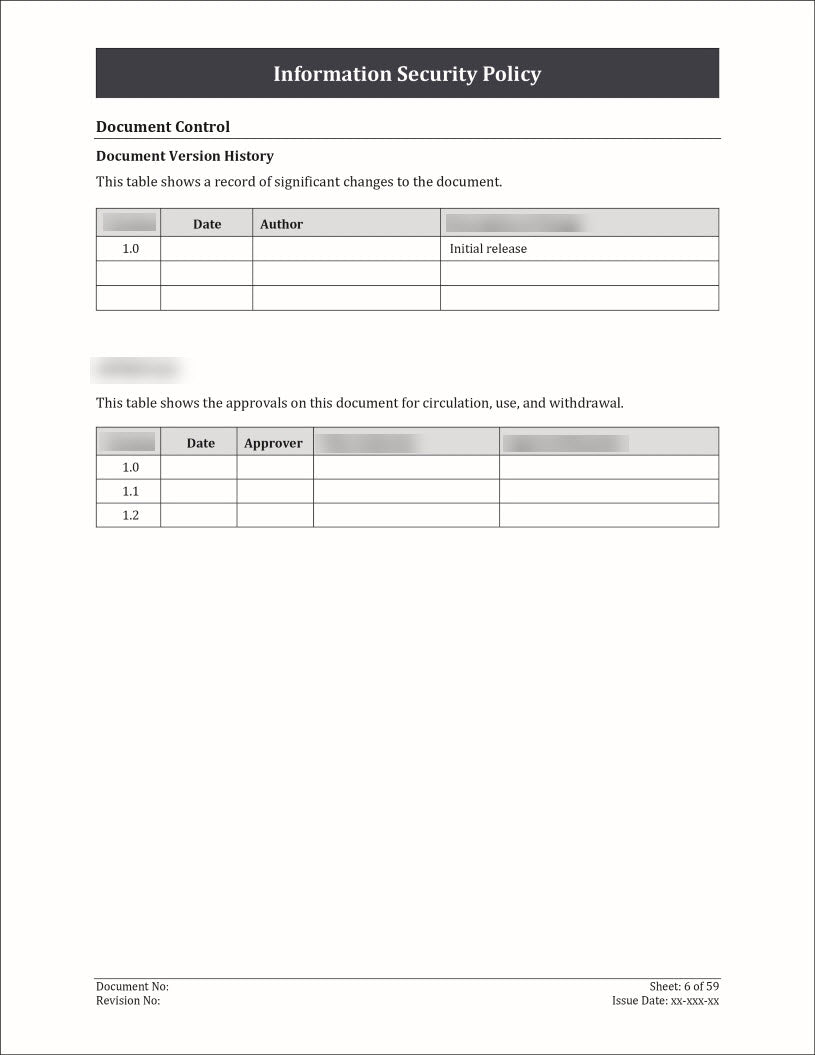
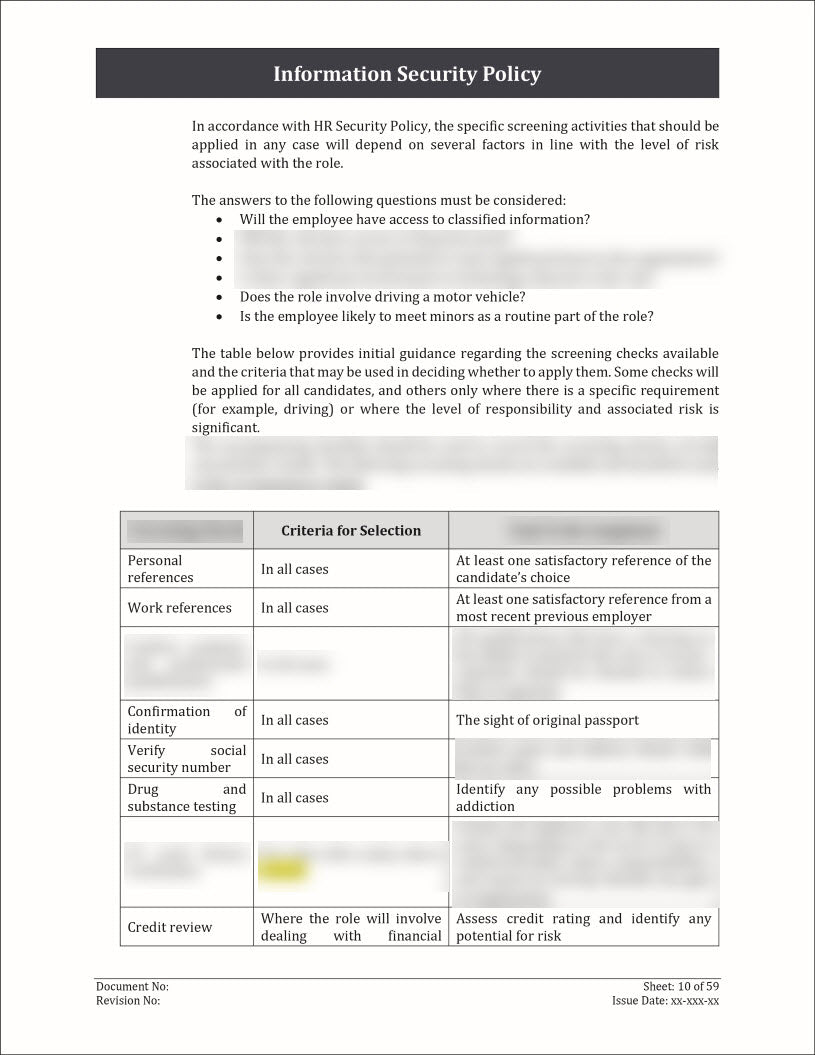
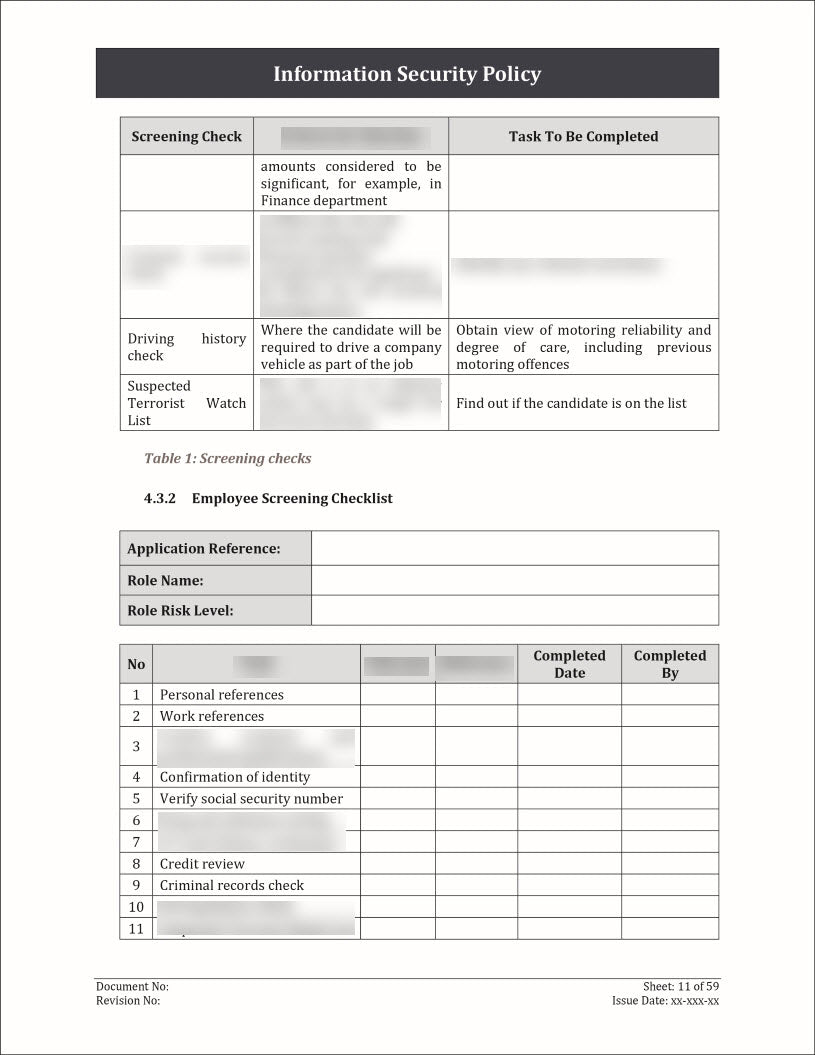
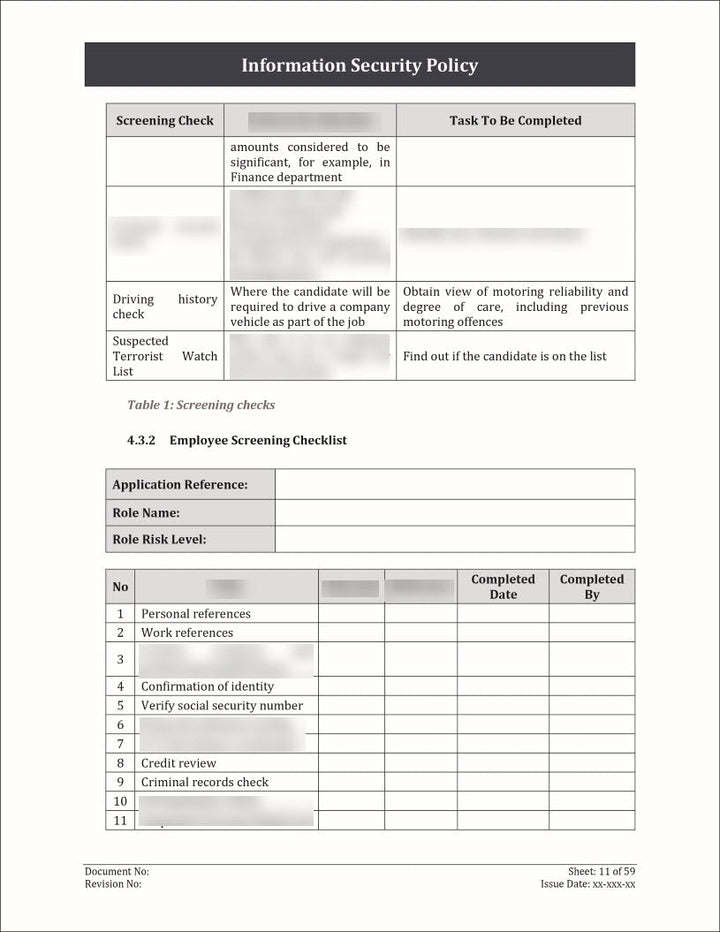
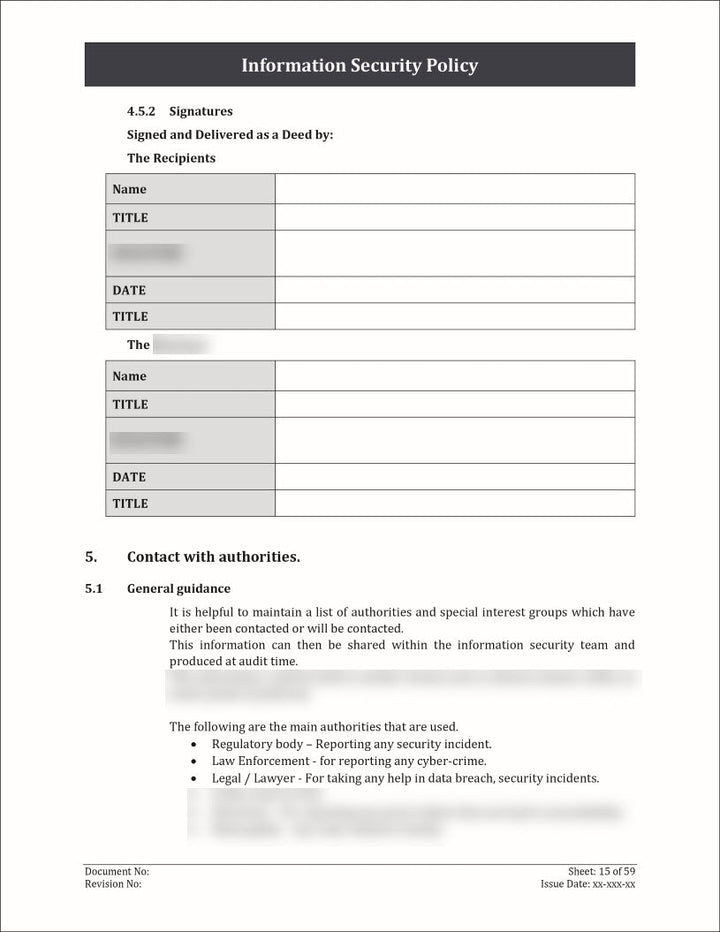
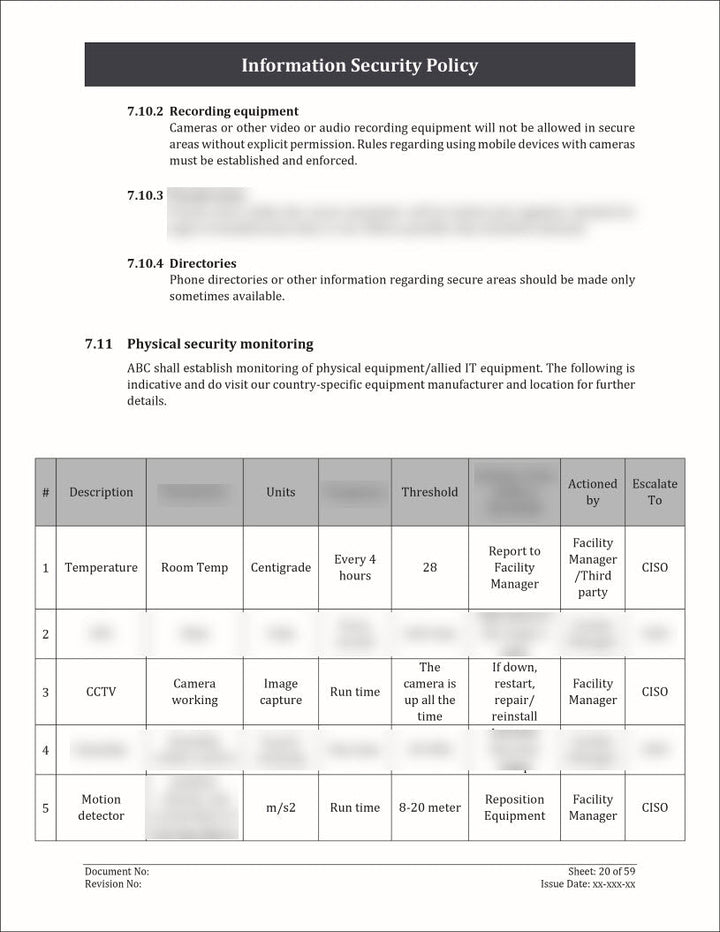
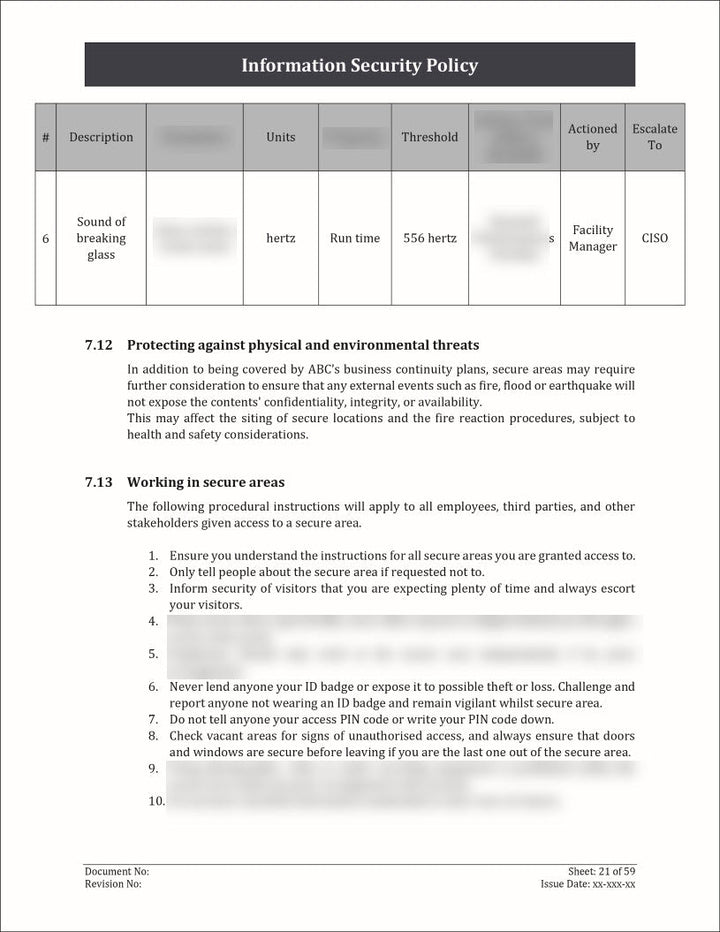
An Information Security Policy Template is a pre-designed document that outlines the guidelines, principles, and rules for protecting an organization's information assets.
It serves as a framework to establish and communicate the organization's commitment to information security and provides guidance to employees on how to handle sensitive data and mitigate risks.
Format: MS Word
Features:
- Policies for Information Security: Document and track the information security policies in place for each asset, ensuring compliance with industry standards and regulatory requirements.
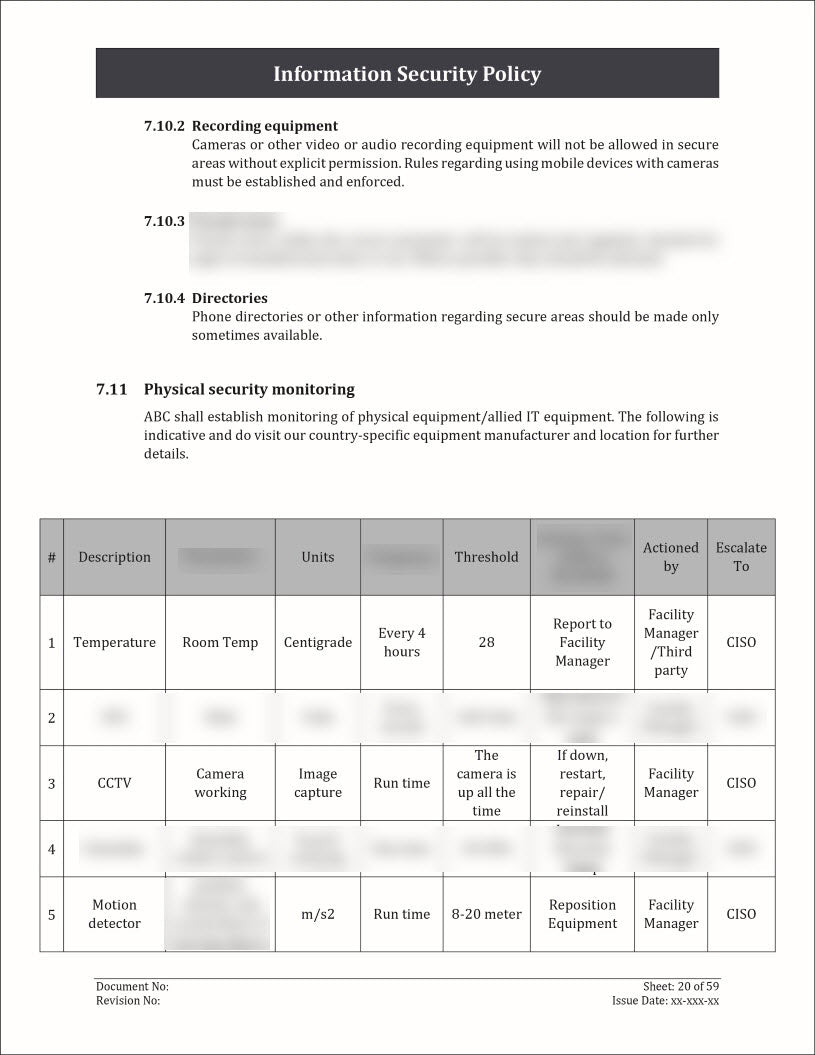
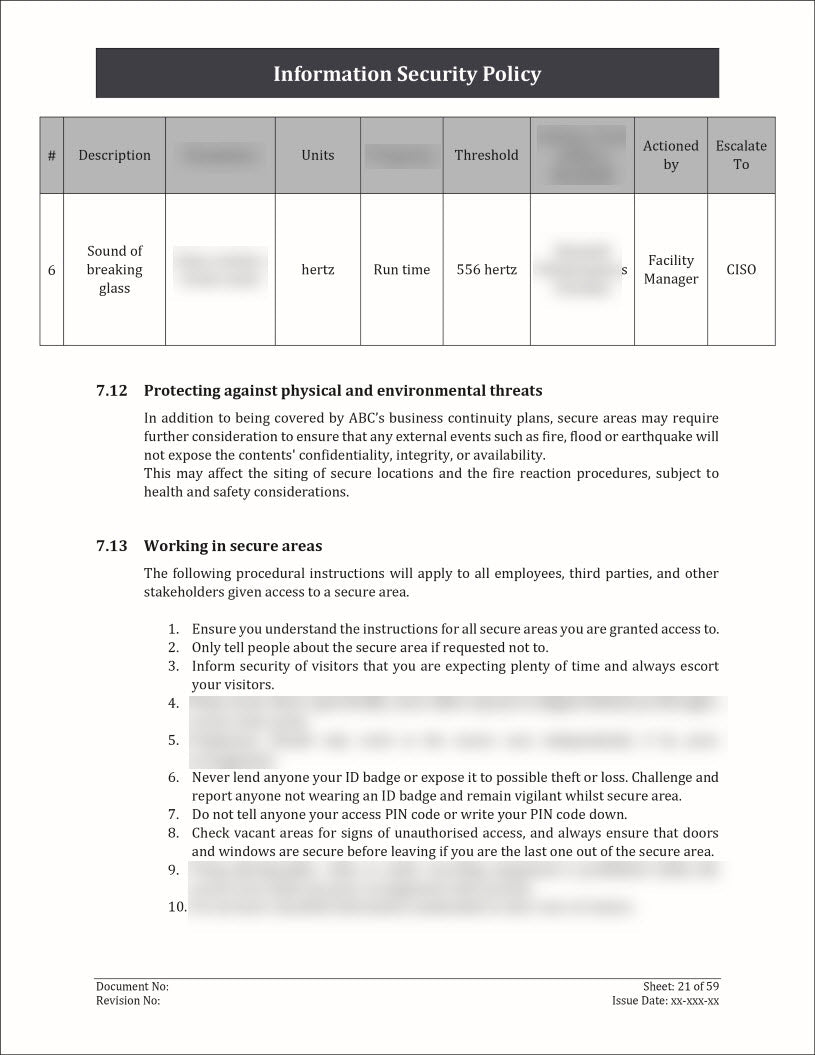
- Physical Security: Capture information about the physical security measures implemented for each asset. This can include details about access controls, surveillance systems, security personnel, and any other measures in place to protect the physical integrity of the asset.
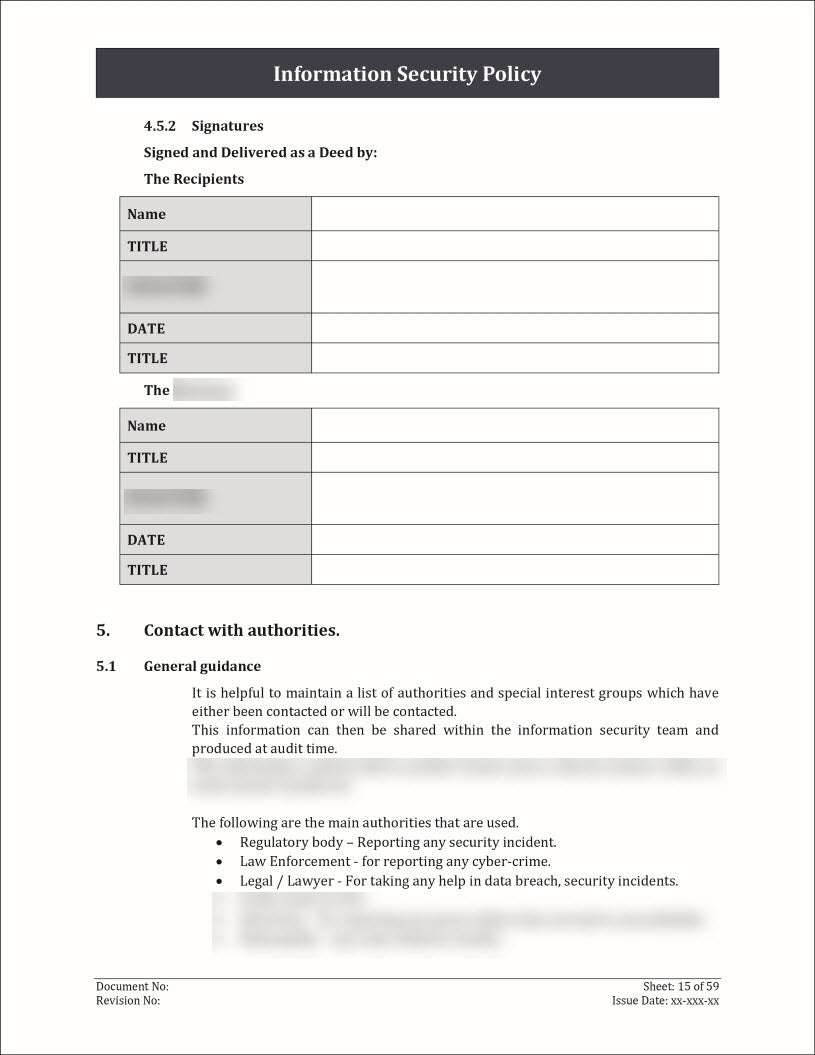
- Contact with Authorities: Maintain a record of contact information for relevant authorities or regulatory bodies associated with each information asset. This can include emergency contact numbers, incident reporting channels, and any other relevant points of contact.
Template Details:
The template includes the following details:
- Information Security Communication
- Policies for Information Security
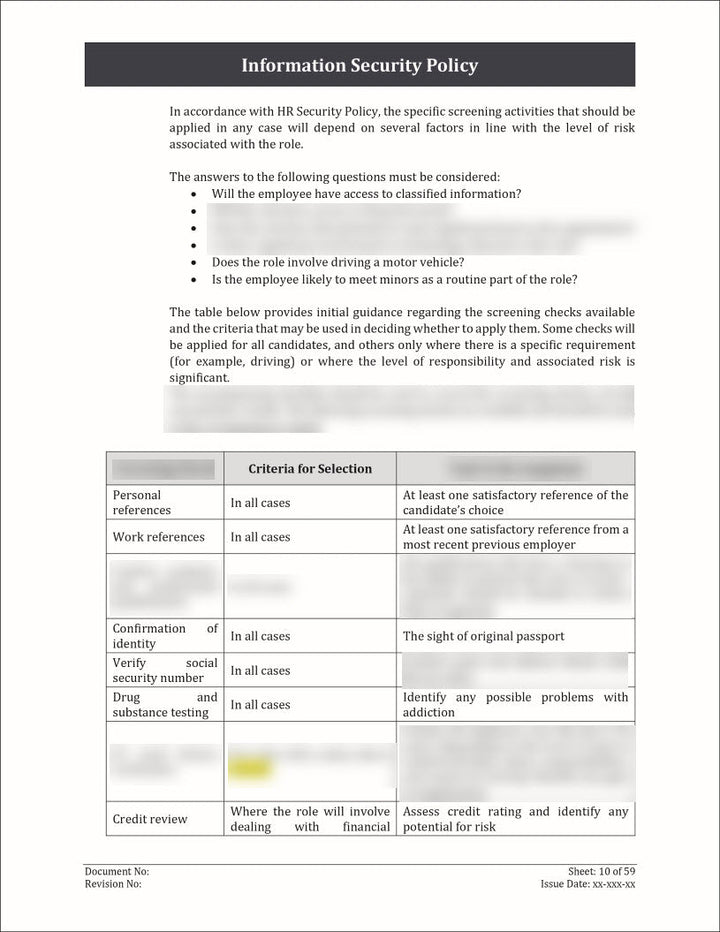
- People Security
- Contact with Authorities.
- Contact with Special Interest Groups
- Physical Security
- Remote Work
- System Access Security
- Application Security Requirement
- Password Security
- Asset Security
- Data Management
- Change and Development Management
- Logging and Monitoring
- Business Continuity and Disaster Recovery
- Security Incident Response
- Risk Management
- Cabling Security
- Vendor Management
- Managing Information Security in the Information and Communication Technology (ICT) Supply Chain
- Privacy and Protection of Personal Identifiable Information (PII)
- Independent Review of Information Security
- Compliance with Policies, Rules and Standards for Information Security
- Exceptions
- Enforcement
- Responsibility, Review, and Audit
- Threat Intelligence
- Protection Against Malware
- Information Security in Project Management
- Information security Awareness, Education, and Training
- Disciplinary Process
- Responsibilities After Termination or Change of Employment.