ISO 27001: Template For Access Control Policy
These policies are essential for ensuring that an organization's data and information systems remain secure and intact. These policies specify the rules and procedures that are used to grant or deny access to resources depending on an individual's identity, their role and permissions.
Access Control Policy: It's Importance
The template of an access control policy is essential to maintaining the confidentiality and security of information systems and data in any organization. There are many reasons to have an access control policy.
1. Protection Against Unauthorized Access: An access control policy will ensure that only individuals with the proper authorization can access sensitive data and resources. The policy reduces the risk of insider threats and data breaches by defining roles, user identities and permissions.
2. Enhanced Data Security: A policy of access control allows organizations to set different levels of user access. Only those who have the appropriate privileges are able to access and modify sensitive information. Data loss and theft are significantly reduced when critical information is restricted.
3. Regulations Are a Must: There are many industries and jurisdictions that have laws and regulations requiring organizations to comply with access control policies. These regulations are designed to protect sensitive data and consumer information. By having a clearly defined access control policy, organizations can avoid any legal consequences and comply with the regulations.
4. Incident Response and Forensic Analyses: An access control policy will help in the event of an incident or unauthorized access. Logging access attempts and tracking users' activity allows organizations to identify the source and mitigate damage by identifying the source.
5. Safeguarding Intellectual Property: Intellectual Property is important to many organizations. Access control policies help protect intellectual property, by limiting access to only authorized personnel. It ensures the confidentiality and security of sensitive data such as proprietary or trade secrets.
6. Employee Productivity: Access Control Policy can improve employee productivity and efficiency. Employees can concentrate on their work without being distracted by irrelevant information and restricted by unnecessary controls by granting them access to the resources they need.
Implementing Access Control Policy in Your Organization
Let's now discuss how to implement an access control policy in your company. Following are the main steps:
1. Identify Your Security Needs: Assess the information systems and data of your organization to determine what level of protection is required. Take into account the sensitive data you manage, your compliance requirements and any potential risks. You can use this information to help establish your access control policy.
2. Define Roles and Responsibility: Clearly define roles and responsibilities within your organization, and their corresponding access rights. Based on the job responsibilities of each employee, determine who has access to which information and resources. This will allow you to create a hierarchy for access levels and ensure that only the data necessary is available.
3. Create Access Control Policy: Develop policies that describe how access requests will be processed, whether access will be granted or revoked and what individuals can do with their rights. These policies must be aligned with regulatory requirements and industry best practices.
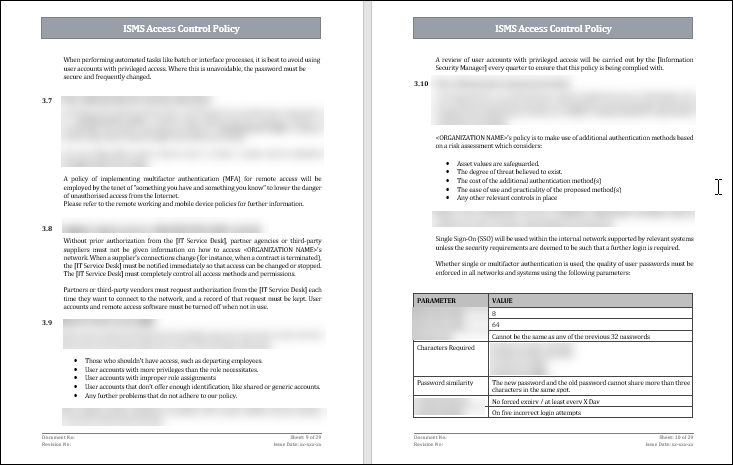
4. Implement Authentication Mechanisms: Implement robust authentication methods to verify the identities of those who access your systems. This includes using biometrics, multi-factor, and strong passwords. Make sure that users must update their passwords on a regular basis and that there are password complexity requirements.
5. Create an Authorization Framework: Establish a framework for authorizing different roles and individuals in your organization. This framework should clearly define what actions individuals are allowed to perform after they have been authenticated.
6. Monitor and Audit Access: Implement tools to monitor and audit the data and systems you use. Review access logs regularly to identify suspicious activities or unauthorized attempts. You will be able to detect security incidents and take immediate action.
7. Provide Awareness and Training: Inform your employees of the risks and benefits associated with unauthorized access. They should be trained on how to handle authentication credentials properly and alert you if they see any suspicious activities.
8. Update and Test Your Policy Regularly: Your access control policies must be reviewed and tested regularly to ensure they are aligned with evolving business needs, evolving threat levels, and regulatory requirements. Conduct periodic penetration tests and security assessments to identify vulnerabilities in your system.
9. Constantly Improve Your Approach: Data security threats and the landscape surrounding them are constantly changing. Keep up to date with the latest technologies and practices in access control. Access control policies should be regularly reviewed and improved to meet new challenges and risks.
By following these steps, your organization can implement a policy for access control and protect its valuable assets. Access control is an important part of your overall cyber strategy and requires constant attention and maintenance.
Monitor and Update the Access Control Policy
Implementing an Access Control Policy is only the first step to ensuring that your organization's data and information systems are secure. In order to keep up with new risks and challenges, it is important to monitor and update your policy regularly.
Consider these key factors when monitoring and updating your Access Control Policy:
1. Regular Audits: Conduct audits regularly to assess the effectiveness of your policy. This includes reviewing access logs and analyzing user rights, as well as identifying anomalies or discrepancies. Audits can help to identify security holes and make sure access controls are working as intended.
2. Incident Response: Create a robust plan for handling any security breaches or incidents that may occur. It is important to define procedures for investigating security incidents, resolving them and communicating with the affected parties. Test and update your plan for incident response regularly to ensure it is aligned with evolving threats and best practices.
3. User Reviews and Recertification: Conduct periodic reviews of users to verify that they still need their access rights. Review user permissions, roles and ensure that they are aligned with the current job responsibilities of employees. Implement a recertification procedure to update and validate user access rights on a regular basis.
4. Training and Awareness: Constantly inform employees of the importance and benefits of proper security and access control. Regularly conduct training sessions for employees to update them on policy updates and any changes. This will ensure that everyone is aware of their responsibilities, and adheres to the access control policies.
5. Stay Up to Date With Regulatory Changes: Be aware of any updates in regulations or compliance requirements. Review your policy on access control to ensure that it is aligned with the regulations.
6. Regular Policy Updates: As technology evolves and new security threats arise, it is important to update your access control policies regularly. Update your policy regularly to include new security measures and address identified vulnerabilities. Also, adapt it to changing business requirements.
7. External Security Assessments: Hire external security experts to perform regular penetration tests and security assessments. These assessments can help you identify any weaknesses in your system and make recommendations to improve security. These assessments will help you make any changes necessary.
8. Collaboration between IT and Security Teams: Encourage collaboration between your IT and Security teams to ensure access control policy updates will be implemented effectively. Communicate regularly with these teams in order to remain aligned with ongoing security initiatives, and address any concerns that they may have.
9. Regular Communication: Communicate regularly updates and changes in the policy of access control to all stakeholders. Employees, managers, and others who interact with data and systems of the organization are included. Transparent communication is essential to ensure that all employees are aware of the changes in policy and know how to comply.
10. Continuous Improvement: Create a culture that encourages continuous improvement in access control policies. Encourage employees and stakeholders to provide feedback and to use that information to improve the policy. Assess the effectiveness of your security measures regularly and look for ways to improve them.
You can protect your company's systems from evolving threats by regularly updating and monitoring your access control policies. Regular policy improvement and evaluation will reduce risks and protect valuable assets. Access control is a continuous process that needs regular attention to keep up with the ever-changing landscape of cybersecurity.
The Conclusion Of The Article Is:
It is important to monitor and update the access control policies in order to ensure the security of the organization's data and information systems. This process involves regular audits, incident-response planning, user reviews, recertifications, training, awareness, regulatory updates, policy updates, external assessments, collaboration between IT and security teams and regular communication.