ISO 27001 Risk Assessment In ISMS
Risk assessment ISO 27001, a process essential to the Information Security Management System (ISMS), helps identify weak areas in protection measures. Risk assessment is a way to determine the existing risks, their impact on your organization, and how to reduce them. This is essential for ensuring you adhere to regulations and protect sensitive information.
Risk Assessment Framework:
- ISO/IEC 2705:2011 – The ISO/IEC 2705:2011 standard provides an information security framework for establishing, implementing, and maintaining an Information Security Management System. This standard explains creating an information security system that protects sensitive data and meets regulatory requirements.
- ISO/IEC 31000:2009- ISO The ISO has jointly developed ISO/IEC 31000:2009, an international management system standard that guides the establishment, implementation, maintenance, and continuous improvement of a risk management system. This international standard is designed to help all organizations understand the benefits of implementing a risk management system.
ISO/IEC 31000 (2009) is Based upon Three Fundamental Principles.
1. The objectives of the organization are clearly defined.
2. Risk management professionals agree on the methods of risk assessment.
3. A set of guidelines can manage an organization's identified risks.
ISO/IEC 31010:2009 - ISO/IEC 31010:2009 is a Standard that defines requirements and gives guidelines on how to use risk management within organizations. It defines risk, "hazard," "threat," and other terms. The standard also identifies various risks and dangers, including business or economic risks, environmental risks, safety-related hazards, security-related threats, health-related hazards, etc.
Penetration Tests for ISO 27001:
The vulnerabilities could be poorly secured websites and applications, inadequate passwords, etc. Penetration testing can identify weaknesses in an organization's IT infrastructure. It will identify weaknesses that hackers may exploit and can help you fix them before they are used.
Types Of Penetration Testing:
1. Network Infrastructure Testing: Network Infrastructure testing is testing an organization's logical and physical networking components to ensure they are working as expected. Networking experts perform network infrastructure testing on networks, routers, and switches to ensure they work correctly.
2. Testing Wireless- Wireless penetration is hacking into wireless networks using specialized hardware and software. This hacking is performed remotely via airwaves or by installing malicious code on an individual device.
3. Social Engineering Testing: You can use this test to determine if your employees share any information. Social engineering is the term used to describe manipulating people and gaining their trust to obtain sensitive information such as passwords, credentials, etc. White hat testers exploit staff members to test their security awareness.
4. White Box Tests: Tests that are based on the knowledge the tester has of the internal structure and workings.
Steps To Implement Risk Assessment:
Create a Risk Management Framework: This includes how to identify risks, who you assign ownership to mitigate risks, and a technique to calculate potential threats. These measures should address the following:
1. Management sets security criteria2. Threat level
3. Situation-based risk assessment
- Evaluate Risks- Assess risks. Assess risks according to their priority by using a matrix of risk assessment. Score risks against your tolerance levels and discuss specific measures to be taken when the risk exceeds tolerance.
- Treatment of Risk- Organizations use different methods to reduce the level of risk depending on their industry and size. Rather than increasing expenditures to reduce the impact, you can modify the risk and turn it into an opportunity. Here are some commonly used risk management options:
2. Outsource to a third party the responsibility of managing the risk
3. Ignore a risk that has little or no impact on your organization
- Report on Risk Assessment- The report on risk assessment summarizes the impact of not identifying and addressing risks, the causes of each risk type, and measures taken to mitigate those risks.
These are the Two Most Important Risk Assessment Reports:
1. Statements of Applicability (SOA): SOA documents measures taken or not taken to mitigate risks and the reasons behind selecting those measures. It is also important to keep track of the progress made in implementing standards.
2. Risk Treatment Plan: A plan for risk management outlines the steps an organization will take to minimize or prevent potential risks from affecting their business. This will help you minimize the damage to your business and ensure it stays afloat.
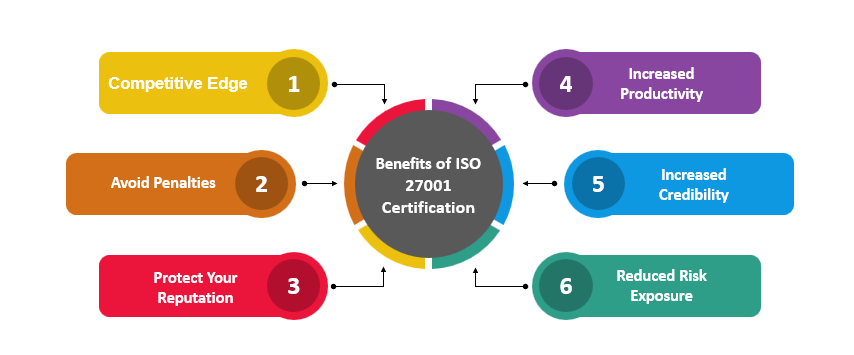
What are the Benefits of ISO 27001 Certification?
- Competitive Edge: ISO27001 Certification helps implement the best security practices, builds trust with clients, and makes you stand out amongst your competitors.
- Avoid Penalties: IBM estimates the cost of a data breach at $2.63million. ISO27001, an internationally accepted standard in information security, allows organizations to avoid regulatory penalties for non-compliance.
- Protect Your Reputation: By not obtaining ISO27001 certification, your company may be at risk for cyber-attacks and other vulnerabilities, which can have catastrophic consequences such as identity theft or lost data. ISO27001 certification will help protect your company from cyber-attacks and ensure you've taken all the necessary measures to safeguard your data.
- Increased Productivity: The security infrastructure expands with the growth of the business. This standard identifies the responsibilities for handling different types of risks, which reduces confusion and improves productivity. The organization can focus more on its growth when less time is wasted dealing with security threats.
- Increased Credibility: You can increase your ISO certification credibility by having an external auditor verify that all the requirements have been met.
- Reduced Risk Exposure: This ensures the company will have a lower chance of an accident or incident. It is achieved by performing regular management audits and reviews, creating emergency plans, keeping records of hazardous substances, and training staff on handling these risks.



