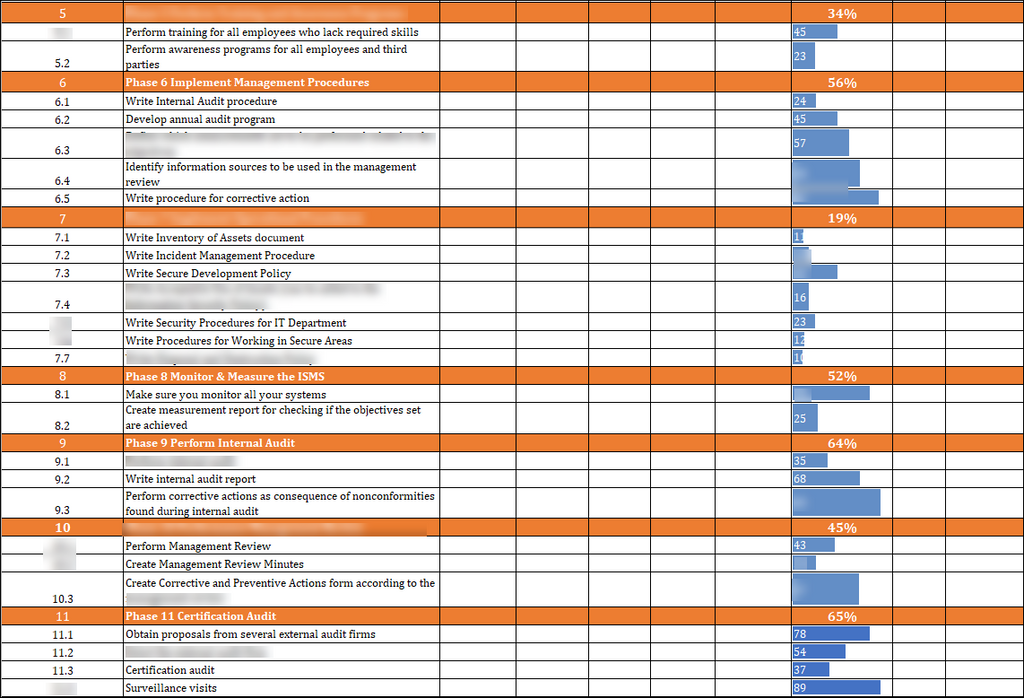
ISO 27001:2022 Project Plan: The Power Comprising Strategic Project Planning
The ISO 27001-2022 Project Plan is an organized and comprehensive document that outlines the tasks, activities, resources, and timelines necessary to implement the ISO 27001-2022 standard in a company. The project plan is a road map that guides an organization through the ISO 27001:2022 certification process.
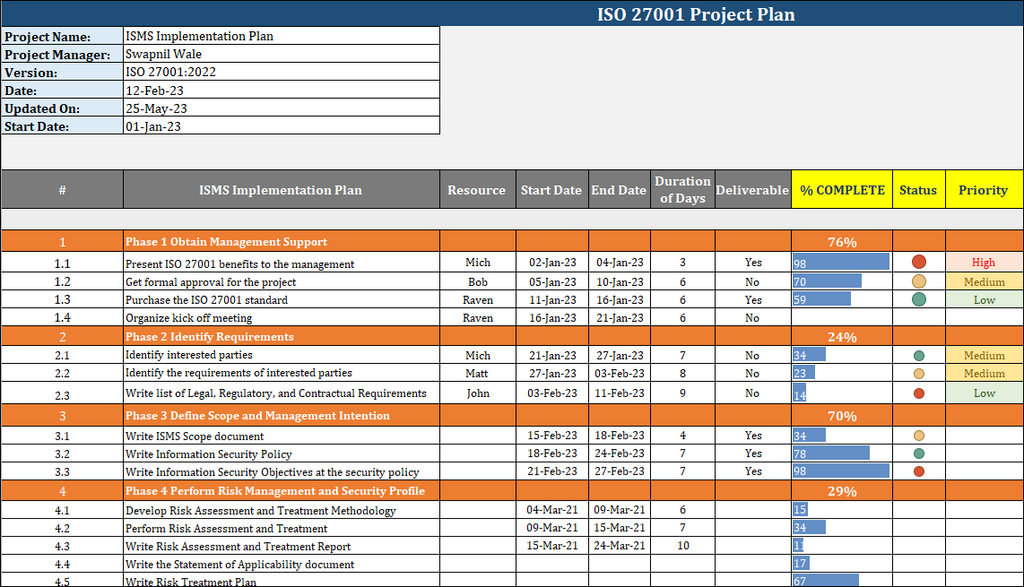
The Scope Of The Project
It is important to first define the project's scope before embarking on your journey towards ISO/IEC 27001 Certification. The scope of your project will help you determine the boundaries and the extent of your project. This way, all important areas can be addressed, and nothing is overlooked.
Consider the following factors when determining the scope of your 27001 project:
1. Size and Complexity of The Organization: Determine the departments, units, or processes included in the scope by assessing the size and complexity of the organization. In order to ensure that the scope of work is realistic and manageable, it is important to strike a balance between inclusiveness and practicality.
2. Legal and Regulatory Requirements: Consider any legal or regulatory obligations that your organization has to comply with. These requirements can vary based on your industry, location, and type of data you manage. Be sure to include all aspects of legal and regulatory compliance.
3. Information Assets and Data Flow: Analyze your organization's information assets, and the data flows that are associated with them. Identify assets needing protection and the systems or processes associated with their lifecycle. This analysis will allow you to determine the boundaries of your projects and ensure all assets and data flow are considered.
4. External Stakeholders and Dependents: Take into consideration any external stakeholders or dependents that could impact your security. Third-party vendors or partners could access your data or systems. It is crucial to include these external factors as part of the scope in order to provide comprehensive coverage.
Document the scope of your project in your project plan once you've defined it. Clearly outlining the objectives and boundaries of the project can help you guide your implementation and ensure that it is focused and practical.
Project Timeline Milestones
It is essential to create a project timeline and set milestones to complete an ISO/IEC 27001. A clearly defined timeline will help you manage resources efficiently, track your progress, and keep the project on schedule. Setting milestones also gives the team a feeling of accomplishment and motivation.
Here are a few steps to take into consideration when setting up milestones and a timeline for your 27001 project:
1. Estimate the Overall Project Duration: Consider the project's scope, complexity, resources, and other factors that may affect timeliness. Be realistic and plan for any delays or unexpected circumstances.
2. Divide the Project Into Phases: Break the project down into distinct stages or phases based on activities and tasks. The phases of a typical 27001 project are planning, risk assessments, control implementations, documentation, certification preparation, and training.
3. Assign Deadlines and Responsibilities: For each deliverable or task, set and assign responsibilities. Make sure the deadlines you set are realistic and that they consider any interdependencies or dependencies between tasks.
4. Mark Important Milestones: These milestones should mark key project achievements or points of progress. They can include completing the risk assessment, finalizing the documentation for the information security system (ISMS), conducting internal audits, and preparing the certification audit.
5. Review and Update Your Timeline Regularly: Monitor the progress of the project and review and update it as necessary. This will allow you to identify any delays or problems early and make adjustments that keep your project on track.
Don't forget to share the timeline and milestones with all stakeholders, including the team, the management, and the external auditors. It will help to ensure that all stakeholders are aware of the progress and deadlines for the project.
Roles and Responsibilities for Team Members
Each team member must clearly define roles and responsibilities to complete an ISO/IEC 27001 Project. Each team member must understand what they are expected to do and maintain accountability.
Consider these roles and responsibilities:
1. Project Manager: A project manager is a key player in the overall project. They oversee and coordinate all aspects. They are responsible for:
- Develop the project plan.
- Monitor the progress of your project and make sure it stays on track.
- Budgets and resources management.
- Communication with project stakeholders and resolution of any issues.
2. Information Security Officer (ISO): The Information Security Officer (ISO) is in charge of implementing and maintaining an information security management system. They are responsible for
- Risk assessments and security controls
- Develop policies and procedures for protecting information assets.
- Monitoring compliance with ISO/IEC 27001 Standards
- Maintaining and updating ISMS documentation.
3. IT Manager: IT managers are responsible for all technical aspects of a project.
- Implementing and managing security measures and controls.
- Assuring confidentiality, integrity, and availability of data and information systems.
- Manage access controls and privileges for users.
- Keep up with the latest security threats and technology.
4. External Auditor: An external auditor is often involved in the ISO/IEC 27001 standard project to ensure that the organization adheres to the standards. They are responsible for:
- Independent audits and assessments
- Verifying the effectiveness and implementation of the ISMS.
- Making recommendations for improvements and remediation.
- After the successful completion of an audit, the certification or attestation is issued.
You can make sure that everyone works towards the same goal by clearly defining each member's role and responsibilities. This will ensure that the project moves forward smoothly. To ensure effective collaboration, regular communication, and coordination between team members are essential.
Monitoring and Evaluation Procedures
The success of ISO/IEC 27001 projects depends on the monitoring and evaluation procedures. These procedures are designed to ensure that information security measures implemented by the organization are effective, and that its information assets are properly protected.
The following are the key steps in monitoring and evaluating a project:
1. Define Key Performance Indicators: It is essential to define KPIs which will be used to measure the effectiveness and efficiency of implemented controls. These KPIs can include metrics like the number of incidents of information security, the percentage trained employees, and the compliance level with ISO/IEC 27001.
2. Establish Monitoring Mechanisms: Implement monitoring systems to collect relevant data about the KPIs identified. These can include regular audits of security, incident reporting systems and employee surveys. The data collected will give insight into the organization's security posture and identify areas for improvement.
3. Conduct Regular Risk Assessments: This will help identify any new threats, vulnerabilities and risks that may affect the organization's data assets. This will allow you to determine whether additional security controls or measures are needed or if the existing ones need to strengthen.
4. Evaluate Compliance: Regularly assess the level of compliance with ISO/IEC 27001 and internal policies. Internal audits and assessments can be conducted by the compliance officer, or external auditors.
5. Continuous Improvement: Drive continuous improvement by using the results of monitoring and evaluation procedures. Corrective actions and improvements to processes can be taken in order to address any weaknesses or areas of improvement. Review and update security controls, policies, and procedures regularly to keep up with new threats and technology.
6. Communication and Reporting: Regularly report the results of the monitoring and evaluation procedures, to all relevant stakeholders such as senior managers, members of project teams, and employees.
Implementing robust monitoring and evaluating procedures allows an organization to assess the effectiveness and efficiency of its controls for information security and make improvements necessary to protect their valuable information assets.
Conclusion
The ISO 27001 Project Plan is the foundation of an organized and systematic approach to achieve compliance with the ISO 27001 standard. It is a set of clearly defined steps and activities which collectively improve an organization's security posture.



