GDPR Cover Letter To Portability Response Template
Introduction
For businesses and organizations, handling GDPR data portability requests is not just about compliance; it's an opportunity to build trust and demonstrate your commitment to protecting customer data. Crafting a well-structured response is vital, and that's where our GDPR Cover Letter to Portability Response Template comes into play. The portability of data refers to personal data without implying ownership of said data.
Scope and Purpose
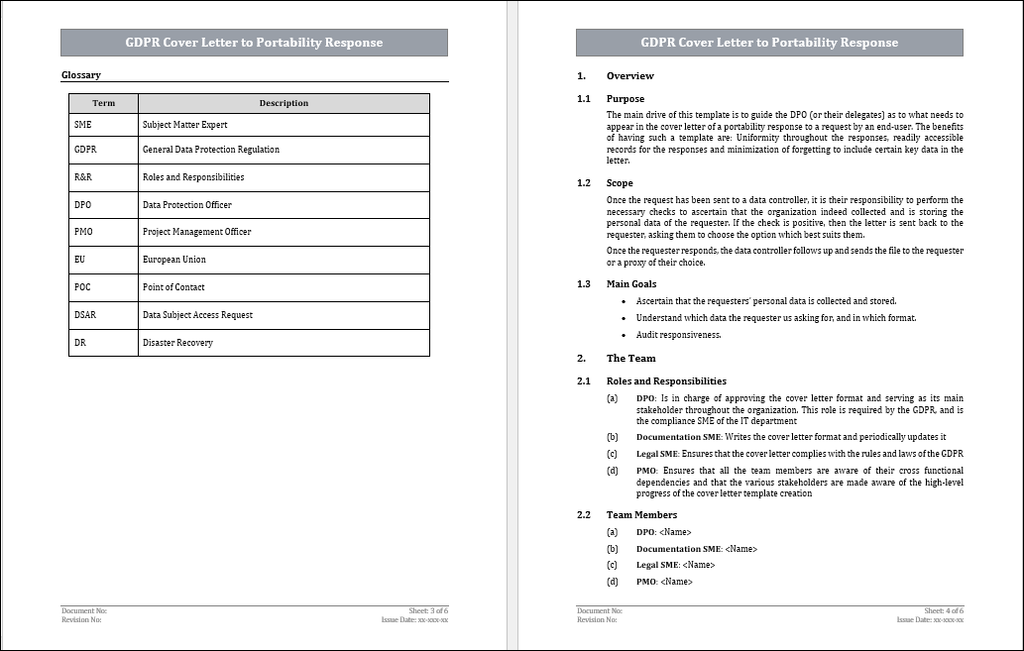
Once the request has been sent to a data controller, it is their responsibility to perform the necessary checks to ascertain that the organization indeed collected and is storing the personal data of the requester. If the check is positive, then the letter is sent back to the requester, asking them to choose the option which best suits them. When the requester responds, the data controller follows up and sends the file to the requester or a proxy of their choice.
Upon receiving a portability request, the data controllers are required to -
1. Check that the organization has collected and stored the requester's personal data.
2. If it has: Confirm that the organization has in its possession the personal data of the requester.
3. If it hasn’t, Inform the requester that none of their personal data is stored on any of the organization’s servers.
4. Keep a record of the request, its response, and any further communication with the requester. This is required for audits.
Required Fields in the Cover Letter
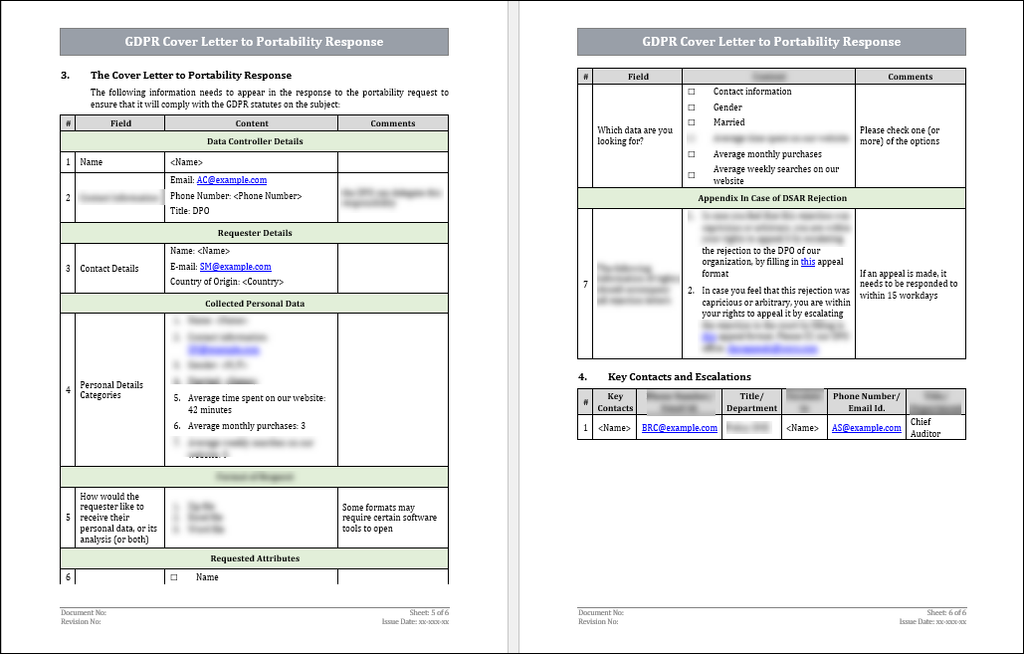
The closure notice should include the following fields –
1. The details of the responder (or data controller)
2. The basic details of the requester.
3. Which attributes of the personal data are stored?
4. Format options for sharing personal data.
5. A blank field asking the requester which of the collected attributes should be in the file.
6. In case of a rejection, Inform the end-user of their right to escalate the request to the country's courts to enforce their request.
Obligations of the Data Controller
1. Ask the requestor how they would like to receive their personal data or its processed analysis. E.g., zip file, Word document, Excel spreadsheet, etc.
2. In case of a rejection letter, notify the data subject of their right to appeal the decision to the local supervisory authority.
3. Send a query to the requestor, asking them which attributes of their personal data they are asking to receive. E.g., Average monthly purchases on the data controller’s website, Average time spent on the website, gender, contact information, etc.
4. Rectify any mistakes regarding the personal data, subject to an inquiry and validation of the request.
Term Definitions
What is a Data Controller?
An organization or person who determines the use of the collected personal data from the data subjects. The data controller owns the collected personal data, decides in which ways it will be processed and bears the sole responsibility for safe keeping it.
What is personal data?
Any type of unique data which relates to an individual data subject. This can include such information as: Name, phone number, Email address, ID number, health records, political opinions, IP address, etc.
What is the processing of personal data?
Any act that is performed on the collected personal data of all the organizations’ data subjects. This may include such actions as storing the data, analyzing it in any way to extract insights or deleting it once it’s no longer required.
What is a data subject (also known as an end-user)?
Any person who created a unique username on the organization’s website, thus giving them the possibility of using that username to perform certain tasks and use features offered on the website.
What is a data breach?
Any intentional or unintentional security incident which involves the sharing of personal data with any unauthorized element. Sharing of personal data may include the viewing, copying, stealing, or altering of the personal data.
Key Takeaways / Conclusions
1. The data controller should ask the requestor if they would like the response to be password-protected.
2. A confirmation of receiving the request should be sent within 1-2 workdays of receiving it.
3. The response should be sent in a timely manner.
4. There isn’t a standard format that the data controllers should abide by, but it should be in a machine-readable format.


