GDPR Annex 4 - Standard Contractual Clauses for the Transfer of Personal Data Processor to Controller
Introduction and Background
What is a data controller?
An organization or person who determines the use of the collected personal data from the data subjects. The data controller owns the collected personal data, decides how it will be processed and bears the sole responsibility for safekeeping it.
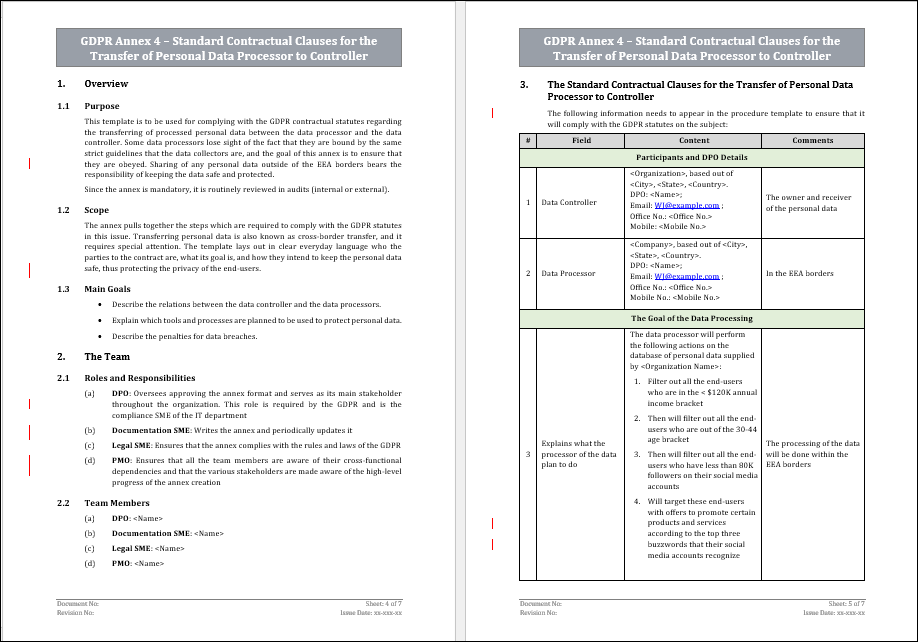
What is a data processor?
A person or organization which was hired by the data controller to act as their proxy in all matters of handling the personal data which was collected by the data controller. This may include such tasks as storing, retrieving, or analyzing it.
GDPR Reference
Organizations participate in joint-partner ventures with the goal of sharing information and processing to use the outcome for separate or joint services. The sharing of information between two or more organizations, regardless of whether it’s within the EEA or outside of it, is a data transfer.
The SCC is required to appear in the joint-partner contract, and it covers the purpose and means of the processing of personal data. The main goal of the SCC is to ensure that all parties share the responsibility of safeguarding personal data, during and after the transfer. Any auditor may request to review the SCC in the scope of an internal or external audit.
Term Definitions
What is a data subject (also known as an end-user)?
Any person who created a unique username on the organization's website, thus giving them the possibility of using that username to perform specific tasks and use features offered on the website.
What is personal data?
Any type of unique data which relates to an individual data subject. This can include such information as Name, phone number, Email address, ID number, health records, political opinions, IP address, etc.
What is the processing of personal data?
Any act that is performed on the collected personal data of all the organizations’ data subjects. This may include such actions as storing the data, analyzing it in any way to extract insights or deleting it once it’s no longer required.
What is a data breach?
Any intentional or unintentional security incident, which involves the sharing of personal data with any unauthorized element. Sharing of personal data may include the viewing, copying, stealing, or altering of the personal data.
Scope and Purpose
The sharing of the data is standard practice amongst data controllers and processors and is done so to allow the processing of the data to be done by an organization that specializes in it.
Types of Processed Personal Data
Examples -
1. Name
2. Phone number
3. Email address
4. IP address
5. ID number
6. Marital status
7. Number of children
8. Annual income
9. Political opinions
10. Religious beliefs
11. Sexual orientation
Obligations of the Data Processor
1. To comply with all the GDPR statutes, same as what the exporter has committed to.
2. To immediately notify the controller of any data breaches.
3. Ensure that the shared personal data stays safe and secure, by using agreed upon tools and processes.
4. Store the data only until it has served its purpose, and no longer than that.
5. Do not use the personal data outside of the stated purpose of the agreement.
6. Respond within a timely manner to any data subject justified requests that have been submitted to the data controller.
Instructions from the Data Controller
The data controller will perform periodic audits, both scheduled and un-scheduled, to confirm that the data processor complies with the GDPR statutes and stays within the scope of the agreement.
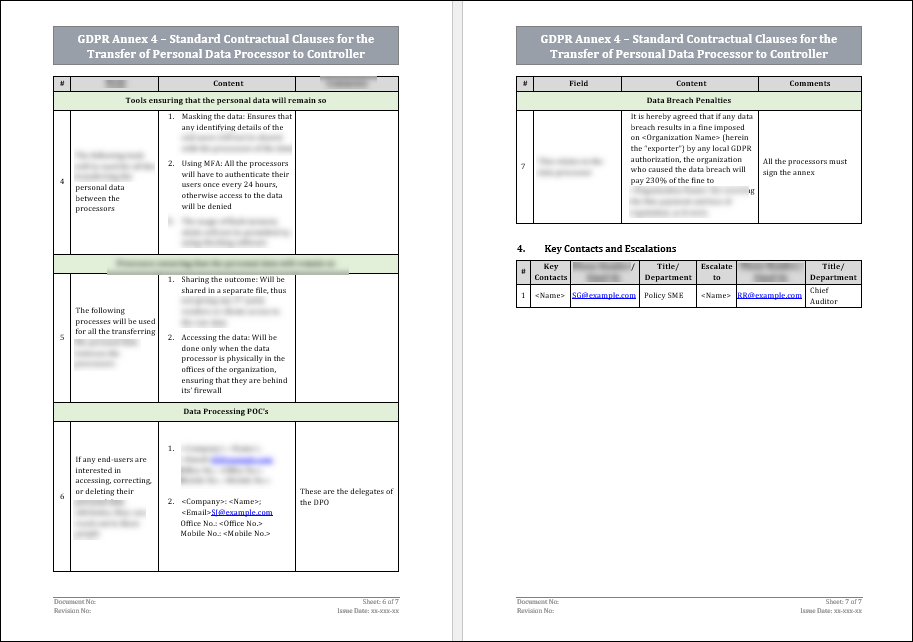
Confidentiality and Security Measures
The data processor must commit, within the scope of the agreement, to safeguard the personal data of the data subjects and to store it for no longer than is required for it to serve its purposes.
Tools -
1. Using cloud-based data: Using only the data stored on the cloud will ensure that any process made by one processor will be used by the others, thus ensuring that no data duplicates will be mistakenly made.
2. Encryption: All the processors will have a key to unlock the data, and this key will be rotated every 12 hours. The encryption tool will keep a log that captures who opened the data files, when this happened and where they were.
3. Storage access restrictions: Since all the personal data will be kept on the data controllers’ cloud, access to it will be given to specific individuals in the data processors’ organizations.
Processes -
1. No downloading of the data: The data on the cloud won’t be able to be downloaded by any of the processors.
Assistance to the Data Controller
The data processor is obliged to follow the same GDPR statutes that the exporter committed to when it first started to collect personal data of its data subjects. This includes responding in a timely manner to their DSAR’s, while using clear everyday language.
In case of a justified request to erase personal data, the exporter shall include the servers of the importer on the list of databases that must expunge the personal data. The importer will send a validation of the erasure to the exporter once it has followed the request. The same shall apply to any rectification request for personal data.
Sub Processing
The contract may include the rights of the data processor to engage with other organizations in order for them to assist with the processing of the personal data. These sub processors shall take upon themselves all the clauses which the data processor has, and it must be made clear that the data processor is accountable for all the actions taken by these sub processors. The data processor must ascertain that these clauses are adhered to by performing periodic and surprise audits of the sub processors.
Data Subjects Requests and Complaints
The data processor is obliged to follow the same GDPR statutes that the controller committed to when it first started to collect the personal data of its data subjects. This includes responding in a timely manner to their DSAR’s, while using clear everyday language. In case of a justified request to erase personal data, the exporter shall include the servers of the importer on the list of databases that must expunge the personal data. The importer will send a validation of the erasure to the exporter once it has followed the request. The same shall apply to any rectification request for personal data.
Terminating the SCC
The termination of the agreement can be done by either party to the joint venture at any given moment. The fine, duration of notice, etc. need to be included in the contract between the parties. The termination of the SCC must include the deletion of all the personal data by the data importer, both on the primary and backup servers.


