GDPR Annex 2 - Standard Contractual Clauses For The Transfer of Personal Data Controller To Processor Template
Data Transfer Purpose
Data controller organizations frequently outsource the task of processing the personal data of their data subjects, with the goal of paying the data processors to perform certain tasks. The sharing of information between the data controllers and processors, regardless of if it’s within the EEA or outside of it, is a data transfer. The SCC is required to appear in the contract, and it covers the purpose and means of the processing of personal data. The main goal of the SCC is to ensure that all parties share the responsibility of safeguarding the personal data, during and after the transfer. Any auditor may request to review the SCC in the scope of an internal or external audit.
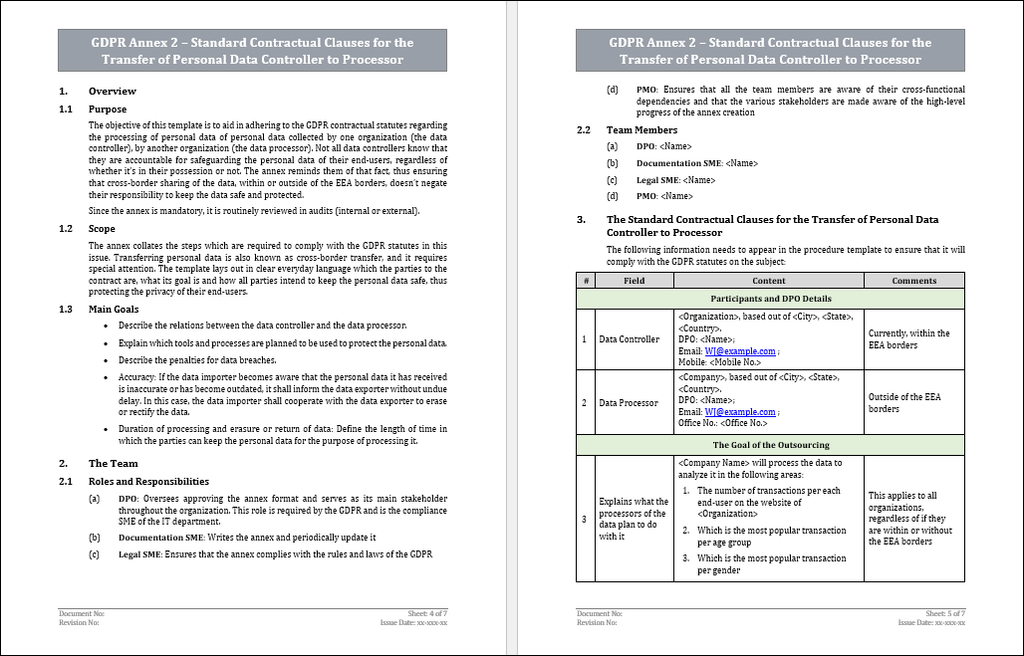
Scope and Applicability
The SCC collates the steps which are required to comply with the GDPR limitations in this issue. Transferring personal data is also known as cross-border transfer, and it requires special attention. The SCC lays out in clear everyday language who the parties to the data transfer are, what its goal is and how all parties intend to keep the personal data safe, thus protecting the privacy of their end-users. The safeguarding of personal data applies to both the data controller and processor, regardless of if they are within or outside of the EU borders.
Term Definitions
What is a data subject (also known as an end-user)?
Any person who created a unique username on the organization’s website, thus giving them the possibility of using that username to perform certain tasks and use features offered on the website is called a data subject.
What is personal data?
Any type of unique data which relates to an individual data subject. This can include such information as: Name, phone number, Email address, ID number, health records, political opinions, IP address, etc.
What is the processing of personal data?
Any act that is performed on the collected personal data of any and all of the organizations’ data subjects. This may include such actions as storing the data, analyzing it in any way to extract insights or deleting it once it’s no longer required.
What is a data controller?
An organization or person who determines the use of the collected personal data from the data subjects. The data controller owns the collected personal data, decides in which ways it will be processed and bears the sole responsibility for safe keeping it.
What is a data processor?
A person or organization which was hired by the data controller to act as their proxy in all matters of handling the personal data which was collected by the data controller. This may include such tasks as storing, retrieving, or analyzing it.
What is a data breach? Any intentional or unintentional security incident, which involves the sharing of personal data with any unauthorized element. Sharing of personal data may include the viewing, copying, stealing, or altering of the personal data.
Data Protection Responsibilities
1. Each party shall keep the personal data accurate and, where necessary, up to date. The data processor shall take every reasonable step to ensure that personal data that is inaccurate, having regard to the purpose(s) of processing, is erased or rectified without delay.
2. The SCC will furthermore impose the obligation that the data processor shall retain the personal data for no longer than necessary for the purpose(s) for which it is processed. The SCC shall put in place appropriate technical or organisational measures to ensure compliance with this obligation, including erasure or anonymisation of the data and all back-ups at the end of the retention period. The same applies to the data controller.
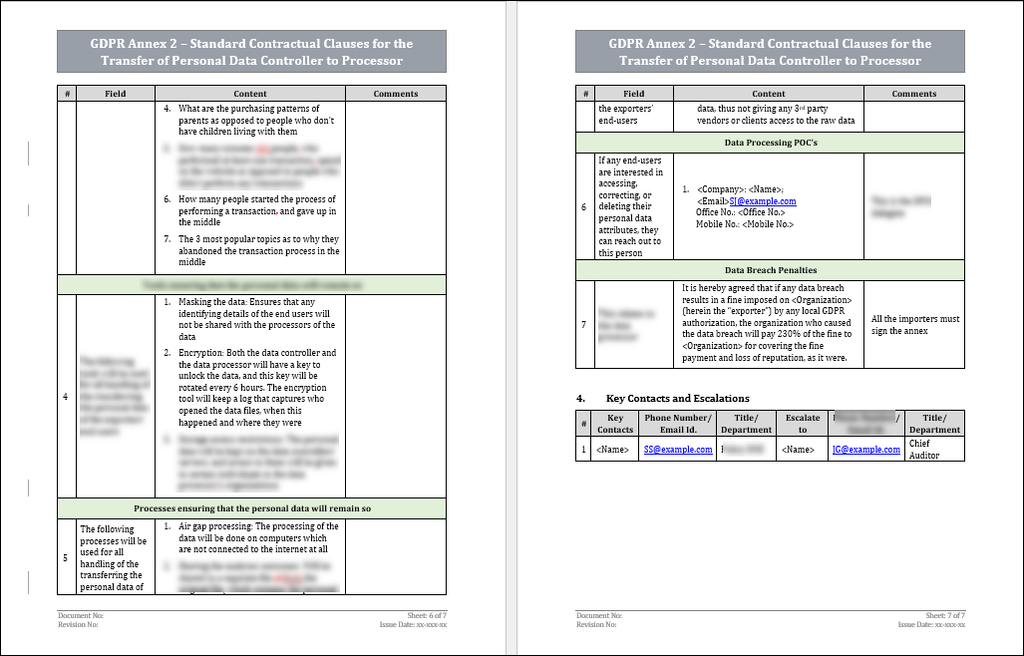
3. Masking the data: Ensures that any identifying details of the end users will not be shared with the importers of the data. These attributes may be requested on a need-to-know basis if any specific concerns or questions arise. This applies to both controller and processor.
4. Encryption: Both the controller and the processor will have a key to unlock the data, and this key will be rotated every 12 hours. The encryption tool will keep a log that captures who opened the data files, when this happened and where they were.
5. Storage access restrictions: The personal data will be kept on the exporters’ servers, and access to them will be given to certain individuals in the importers’ organizations.
The Nature and Goal of the Data Processing
Data processing includes the following activities –
1. Securing: Ensuring that it doesn’t’ fall into the hands of any malicious organizations or individuals.
2. Analyzing: Using collated personal data to analyze certain trends, patterns, and behaviours of certain data subjects. The outcome of this process is to use the information to reduce waste, increase income, etc.
3. Retrieval: Once the personal data is stored, it needs to remain handy in order for it to be used. Retrieving it effectively can assist either party in reducing costs and time.
Types of Processed Personal Data
Examples -
1. Name
2. Phone number
3. Email address
4. IP address
5. ID number
6. Marital status
7. Number of children
8. Annual income
9. Political opinions
10. Religious beliefs
11. Sexual orientation
Data Breach Obligations: Data Processor
The data processor is obligated to immediately notify the exporter if any data breach occurs, regardless of if it was a result of human error, malicious attempts, etc. The notification must include a preliminary report with the following details –
1. Immediate Actions: Assessment of the breach ramifications, what caused the breach and who will be responsible for mitigating its impact and notifying the customers and authorities.
2. General Information: Location, date & time, how it was discovered, the scope of the breach. and the organizations’ details.
3. Details: The specifics of the breach, how the organization plans on dealing with it, and the consequences of the breach.
4. Notification (both the GDPR authorities and the customers): How were they notified, by whom and the POC.
5. Lessons Learned: How can the organization do better in the future, which new tools or procedures are required and personal ramifications in case of a human error.
SCC Compliance Audits
The data controller may conduct audits of the data processor. These can include –
1. Periodic Audits: these include processes adherence, checking that the tools used to ascertain that all the GDPR statutes are being adhered to are being used, safe storage in both primary and backup servers and sites.
2. Ad-Hoc: in case a data breach has been reported, or is suspected.
Key Takeaways/Conclusion
1. The SCC needs to outline the processes aimed at safeguarding the personal data by both the data controller and processor.
2. The SCC needs to outline the tools which will be used to safeguard the personal data by both the data controller and processor.
3. The SCC needs to lay out the fines for any data breaches on the side of the data processor.


